A) 802.1X
B) 802.3
C) LDAP
D) TKIP
E) CCMP
F) WPA2-PSK
H) D) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security administrator is creating a risk assessment with regard to how to harden internal communications in transit between servers. Which of the following should the administrator recommend in the report?
A) Configure IPSec in transport mode.
B) Configure server-based PKI certificates.
C) Configure the GRE tunnel.
D) Configure a site-to-site tunnel.
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A systems administrator needs to install the same X.509 certificate on multiple servers. Which of the following should the administrator use?
A) Key escrow
B) A self-signed certificate
C) Certificate chaining
D) An extended validation certificate
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A penetration tester finds that a company's login credentials for the email client were client being sent in clear text. Which of the following should be done to provide encrypted logins to the email server?
A) Enable IPSec and configure SMTP.
B) Enable SSH and LDAP credentials.
C) Enable MIME services and POP3.
D) Enable an SSL certificate for IMAP services.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A remote user (User1) is unable to reach a newly provisioned corporate windows workstation. The system administrator has been given the following log files from the VPN, corporate firewall and workstation host. 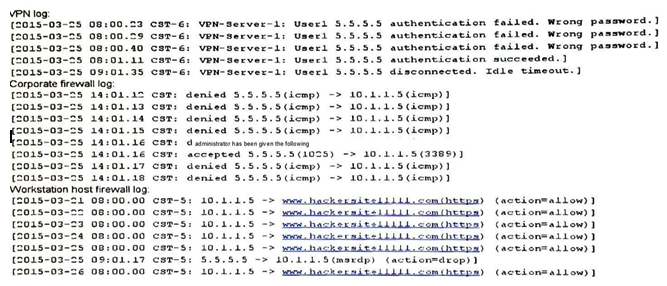 Which of the following is preventing the remote user from being able to access the workstation?
Which of the following is preventing the remote user from being able to access the workstation?
A) Network latency is causing remote desktop service request to time out
B) User1 has been locked out due to too many failed passwords
C) Lack of network time synchronization is causing authentication mismatches
D) The workstation has been compromised and is accessing known malware sites
E) The workstation host firewall is not allowing remote desktop connections
G) C) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network administrator is trying to provide the most resilient hard drive configuration in a server. With five hard drives, which of the following is the MOST fault-tolerant configuration?
A) RAID 1
B) RAID 5
C) RAID 6
D) RAID 10
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security analyst is working on a project that requires the implementation of a stream cipher. Which of the following should the analyst use?
A) Hash function
B) Elliptic curve
C) Symmetric algorithm
D) Public key cryptography
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
In a corporation where compute utilization spikes several times a year, the Chief Information Officer (CIO) has requested a cost-effective architecture to handle the variable capacity demand. Which of the following characteristics BEST describes what the CIO has requested?
A) Elasticity
B) Scalability
C) High availability
D) Redundancy
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following would enhance the security of accessing data stored in the cloud? (Select TWO)
A) Block level encryption
B) SAML authentication
C) Transport encryption
D) Multifactor authentication
E) Predefined challenge questions
F) Hashing
H) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A user is presented with the following items during the new-hire onboarding process: -Laptop -Secure USB drive -Hardware OTP token -External high-capacity HDD -Password complexity policy -Acceptable use policy -HASP key -Cable lock Which of the following is one component of multifactor authentication?
A) Secure USB drive
B) Cable lock
C) Hardware OTP token
D) HASP key
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following would a security specialist be able to determine upon examination of a server's certificate?
A) CA public key
B) Server private key
C) CSR
D) OID
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
As part of the SDLC, a third party is hired to perform a penetration test. The third party will have access to the source code, integration tests, and network diagrams. Which of the following BEST describes the assessment being performed?
A) Black box
B) Regression
C) White box
D) Fuzzing
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which of the following BEST describes a network-based attack that can allow an attacker to take full control of a vulnerable host?
A) Remote exploit
B) Amplification
C) Sniffing
D) Man-in-the-middle
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A forensics analyst is investigating a hard drive for evidence of suspected illegal activity. Which of the following should the analyst do FIRST?
A) Create a hash of the hard drive.
B) Export the Internet history.
C) Save a copy of the case number and date as a text file in the root directory.
D) Back up the pictures directory for further inspection.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
As part of a new BYOD rollout, a security analyst has been asked to find a way to securely store company data on personal devices. Which of the following would BEST help to accomplish this?
A) Require the use of an eight-character PIN.
B) Implement containerization of company data.
C) Require annual AUP sign-off.
D) Use geofencing tools to unlock devices while on the premises.
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company wants to host a publicly available server that performs the following functions: Evaluates MX record lookup Can perform authenticated requests for A and AAA records Uses RRSIG Which of the following should the company use to fulfill the above requirements?
A) DNSSEC
B) SFTP
C) nslookup
D) dig
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A company has won an important government contract. Several employees have been transferred from their existing projects to support a new contract. Some of the employees who have transferred will be working long hours and still need access to their project information to transition work to their replacements. Which of the following should be implemented to validate that the appropriate offboarding process has been followed?
A) Separation of duties
B) Time-of-day restrictions
C) Permission auditing
D) Mandatory access control
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An organization has implemented an IPSec VPN access for remote users. Which of the following IPSec modes would be the MOST secure for this organization to implement?
A) Tunnel mode
B) Transport mode
C) AH-only mode
D) ESP-only mode
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
An office recently completed digitizing all its paper records. Joe, the data custodian, has been tasked with the disposal of the paper files, which include: Intellectual property Payroll records Financial information Drug screening results Which of the following is the BEST way to dispose of these items?
A) Schredding
B) Pulping
C) Deidentifying
D) Recycling
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A security administrator has been assigned to review the security posture of the standard corporate system image for virtual machines. The security administrator conducts a thorough review of the system logs, installation procedures, and network configuration of the VM image. Upon reviewing the access logs and user accounts, the security administrator determines that several accounts will not be used in production. Which of the following would correct the deficiencies?
A) Mandatory access controls
B) Disable remote login
C) Host hardening
D) Disabling services
F) All of the above
Correct Answer

verified
Correct Answer
verified
Showing 241 - 260 of 1164
Related Exams